ZERO TRUST CONTENT DISARM & RECONSTRUCTION (CDR)
Try It Now
Drag and drop a file to have it transformed by Zero Trust CDR
How does it work?
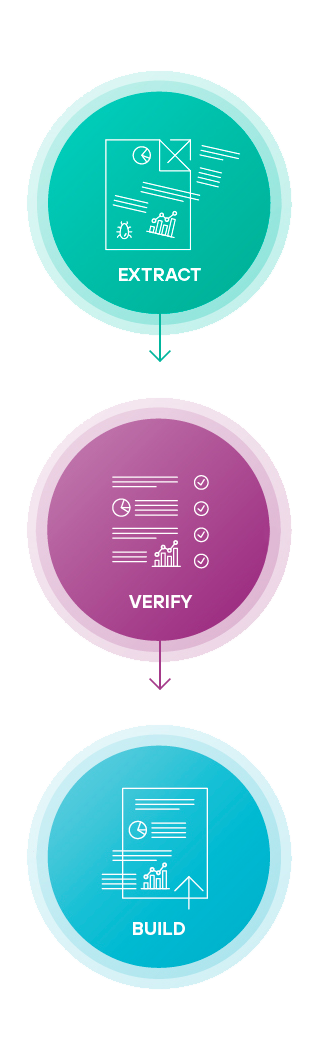
Forcepoint’s Zero Trust CDR is different. Rather than trying to detect malware, it assumes nothing can be trusted. It works by extracting the valid business information from files (either discarding or storing the originals), verifying the extracted information is well-structured, and then building new, fully functional files to carry the information to its destination.
Zero Trust CDR is a game-changer for mitigating against the threat of even the most advanced zero-day attacks and exploits.
Learn more about Zero Trust CDR




File not supported? Contact our team here to organize a demo with the full product.
Benefits
Zero Trust CDR delivers guaranteed threat-free files that are pixel perfect and fully revisable. Meaning that there is no risk from even the most sophisticated attacks.
Zero Trust CDR stops malware, malicious file uploads and protects isolated networks.
No Scanning,
No Sandboxing
No Waiting!
Zero Trust CDR doesn’t use detection, so there’s no waiting for the system to scan content and try to detect known threats.
What’s Next?
When you upload a file, Zero Trust CDR to transforms it. The original is immediately deleted. The transformed file is available for you to download and inspect.
Forcepoint does not retain your file, either in its original or transformed state.





